Wifi Dictionary File
This is a brief walk-through tutorial that illustrates how to crack Wi-Fi networks that are secured using weak passwords. It is not exhaustive, but it should be enough information for you to test your own network’s security or break into one nearby. The attack outlined below is entirely passive and it is impossible to detect provided that you don’t actually use the password that you crack. An optional active deauthentication attack can be used to speed up the reconnaissance process and to get the handshake value. DISCLAIMER: This method is for educational purposes only. It should not be used for illegal activity. The author is not responsible for its use.
Requirements:. A Kali Linux machine (2017.1 preferably).
A which supports monitor mode. Have aircrack-ng utility installed. If aircrack-ng is not installed in your Linux machine, then you can easily install it via below command: sudo apt-get install aircrack-ng Now first step is to recognize your wireless adapter by typing “ iwconfig” in your terminal. Here you can see, wlan0 is your wireless interface and it tells that it supports 802.11, ESSID is off and mode is managed etc. Now second step is to use Aircrack-ng which converts your wireless card into promiscuous monitor mode, it means it can see and receive all network traffic. Here ng means New Generation, because aircrack-ng replaces older suite called aircrack that is no longer supported.
Cracking WiFi - WPA/WPA2 (Aircrack-ng vs coWPAtty) Comparing Aircrack-ng versus coWPAtty, in the time it takes to crack a WPA2 PSK key. If the network key is in the dictionary, its just a question of waiting to process the dictionary file. From here, the attacker can use that key to decrypt the captured data from before, and now is able to.
Now to start the monitor mode, just type “ airmon-ng start wlan0“, which converts your wlan0 into wlan0mon. The next tool is airodum-ng which enables us to capture packets of our specifications.
Start listening to broadcast by nearby wireless routers using your monitor interface by typing “ airodump-ng wlan0mon” in your same terminal. You should see the output similar to above screen. For the purposes of this practical, we will choose to crack the password of our network, “ Chetan Soni“. Remember the BSSID MAC address and channel (CH) number as displayed by, as we will need them both for the further steps.

So Our BSSID address is C4:F0:81:A1:0C:99 and Channel No is 11. As we can see in the screenshot above, airodump-ng displays all of the APs (access points) within range with their BSSID (MAC address), their power, the number of beacon frames, the number of data packets, the channel, the speed, the encryption method, the type of cipher used, the authentication method used, and finally, the ESSID. Resident evil 4 cheats ps2. Now next step is to capture a 4-way handshake because WPA/WPA2 uses a to authenticate devices to the network. You don’t have to know anything about what that means, but you do have to capture one of these handshakes in order to crack the network password. These handshakes occur whenever a device connects to the network, for instance, when your neighbor returns home from work. To capture 4-way handshake, type “ airodump-ng -c 11 –bssid C4:F0:81:A1:0C:99 -w yeahhub wlan0mon” in your terminal.
Here -c stands for Channel, –bssid stands for Mac Address and -w stands for writing the packets into file. You should see the output similar to above screen. Now here you can see in top right corner of above screen, there is no handshake so to get the handshake value instantly, we’ll use deauthentication method in which we’ll forced to send the malicious deauthentication packets to the target for reconnect. To deauthentication the target, type “ aireplay-ng -0 2 -a C4:F0:81:A1:0C:99 -c 84:10:0D:9E:A1:CD wlan0mon” in another terminal. Aireplay-ng is another powerful tool in our aircrack-ng arsenal, and it can be used to generate or accelerate traffic on the AP. This can be especially useful in attacks like a deauth attack that bumps everyone off the access point, WEP and WPA2 password attacks, as well as ARP injection and replay attacks.
Here -a stands for BSSID address of the target and -c stands for station address. A deauth attack sends forged deauthentication packets from your machine Nto a client connected to the network you are trying to crack. These packets include fake “ sender” addresses that make them appear to the client as if they were sent from the access point themselves. Upon receipt of such packets, most clients disconnect from the network and immediately reconnect, providing you with a 4-way handshake as shown below.
You can optionally broadcast deauth packets to all connected clients with “ aireplay-ng -0 2 -a wlan0m0n“. So here, our handshake is “ C4:F0:81:A1:0C:99“.
Once you’ve captured a handshake, press CTRL +C to quit airodump-ng. You should see a.cap file wherever you told airodump-ng to save the capture (likely called yeahhub-01.cap). We will use this capture file to crack the network password. Now the final step is to crack the password using the captured handshake. If you have access to a GPU, we highly recommend using hashcat for password cracking.
Method 1 – GPUHASH.me You can also use a website through which you simply need to upload your.cap file by clicking on Add new task. In 2nd step, click on Next Now select the Basic WPA search package and fill out your email address and then click on SEND. At the end, you’ll get a task id where you can easily monitor your status whether your password they cracked or not. Method 2 – OnlineHashCrack You can also upload your.cap file into website along with your email address and then submit. Here you can upload the.cap file of maximum size is 20MB only.
Dictionary Attack Word List Download
Method 3 – Naive-Hashcat Before to crack the password using, we need to convert our.cap to the equivalent hashcat file format.hccapx. You can do this easily by either uploading the.cap file to or using the tool directly. You can also use website to convert the.cap file into.hccapx file. You can also use utility which is an open source script which you can download it through github by typing “ git clone After downloading the hashcat, go into /src directory and type “ make” command to compile the package. Now run the following command to convert the.cap file into.hccapx format using hashcat.
Command:./cap2hccapx.bin Now copy the.hccapx file to root because we need this file with naive-hashcat script. Now to install naive-hashcat package, type “ git clone Download the dictionary file by typing “ curl -L -o dicts/rockyou.txt Now type “ HASHFILE=./yeahhub.hccapx POTFILE=yeahhub.pot HASHTYPE=2500./naive-hashcat.sh “.
Wifi Dictionary File Download
Naive-hashcat uses various dictionary, rule, combination, and mask (smart brute-force) attacks and it can take days or even months to run against mid-strength passwords. The cracked password will be saved to yeahhub.pot, so check this file periodically.
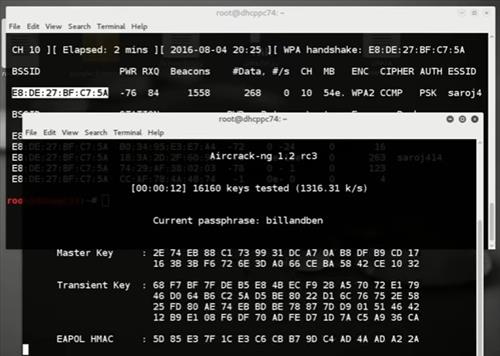
Once you’ve cracked the password, you should see something like this as the contents of your pot file. E30a5a57fc00211fc9fcc3:9c5c8ec9abc0:acd1b8dfd971:Chetan Soni:hackitnow Aircrack-ng can be used for very basic dictionary attacks running on your CPU. Before you run the attack you need a word list. Now copy the same dictionary file into root by typing below command: Note, that if the network password is not in the word file you will not crack the password. To crack the password using aircrack-ng, type “ aircrack-ng -a2 -b C4:F0:81:A1:0C:99 -w dictionary.txt yeahhub-01.cap“. If the password is cracked you will see a KEY FOUND!
Wifi Dictionary File
Message in the terminal followed by the plain text version of the network password as shown below: Yippe, we got the key! Much of the information presented here was gleaned from. Thanks also to the awesome authors and maintainers who work on Aircrack-ng and Hashcat.